A botnet is a network of remote-controlled zombie computers.
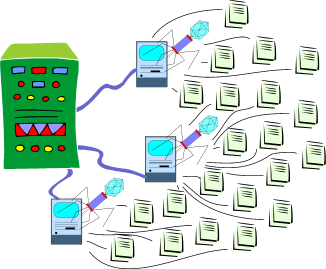
Botnets were slowly constructed during 2004 and 2005 (and continue to be constructed) using viruses and Trojans. In January 2006 Jeanson James Ancheta, a California 20-year-old, pled guilty to controlling a botnet via one IRC Chat![]() channel while selling its services over a second channel. He is yet to be sentenced at this writing (sentencing is scheduled for May 2006). Ancheta used a modified version of the Trojan horse program “rxbot” to build his botnet.
channel while selling its services over a second channel. He is yet to be sentenced at this writing (sentencing is scheduled for May 2006). Ancheta used a modified version of the Trojan horse program “rxbot” to build his botnet.
Past activities for shutting down botnets involved targeting the spam and attempting to get people to clean their computers. This is a slow and often unproductive approach so the newest way of fighting botnets is to attack the control mechanism; generally the IRC channel being used to control the botnet. If the control is taken down then the individual bots sitting on user machines are ineffective. Of course, these computers could be recaptured for later use if the robot programming is sophisticated enough. And, other control mechanisms, not as easily found, could be used to control the bots.
Like all malware, there is a continuous war between the white and black hats.
Summary
- Botnets are networks of compromised computers.
- Botnets can be used for many things and are usually controlled via an IRC chat channel.
| Buffer Overflow | Social Engineering |