In This Issue:
- Users Not Protected
- Viewing File Extensions
- Outlook vs Outlook Express
- Explorer Masquerade
- MS Security
- Y2K Revisit
- Trojans (Downloader [Badman])
- Macro Viruses (WM97/Akuma-D, WM97/Ciao-A, WM97/IIS-U, WM97/Marker-AO, DJ, and DW, WM97/Melissa-BE, WM97/Now-A, WM97/Resume-A, WM97/Smac-E, WM97/Thursday-W and Z, WM97/Vmpck1-DM, XM97/Barisada-A, XM97/Jini-A, XM97/Yawn-A)
- Worms (Timofonica, Gnutella Worm, VBS/NewLove-A, VBS/Fireburn-A, VBS/CoolNote-A, VBS/Scrambler & W32/Scrambler, VBS/LoveLet-AS)
General Security
Users Not Protected. A survey by Central Command (54,091 responses out of 500,000 queries) indicates that 24% of respondents said they don’t update anti-virus software at least monthly; this, despite the recent well-publicized outbreaks. The survey further indicated that in the past year 65% of users had experienced at least one virus/worm and 57% of those resulted in data loss. Some 14% reported over five attacks in a year. The full survey results are published at:
[Link no longer available.]
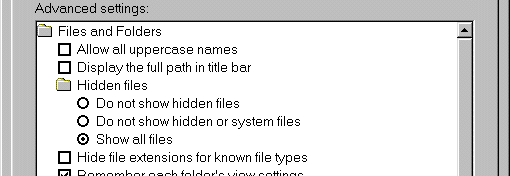
Viewing File Extensions. You’ll note in this issue (and in past issues) that viewing file extensions can be an important part of security (at least for now since Microsoft is working to do away with them ala the Macintosh). How to you make certain you can see extensions? In Windows 98 double click to open “My Computer” and then select “View”|”Folder Options”. Select the “View” tab and then scroll down to the entry that says “Hide file extensions for known file types” and make certain it’s not checked. Click OK and then close the My Computer window. With this move you will now see extensions in file directory windows and the option will be picked up by other Microsoft programs like Outlook.
Outlook vs. Outlook Express. There is some confusion about the press reports for the latest worms. Microsoft has two E-mail programs that have similar names: Outlook and Outlook Express. For a discussion about how the worms affect these programs please see that page in the revised Virus Tutorial.
While you are there, take a look at the next page in sequence which discusses turning the Windows Scripting Host off.
Explorer Masquerade. Several flaws have been discovered in Internet Explorer which could allow a hacker to masquerade as a valid secure web site and potentially, therefore, cause you to enter and send information you would not otherwise send to the hacker. The problem revolves around how IE handles Secure Socket Layer (SSL) transactions; those transactions that typically are performed while the browser is displaying a small padlock icon. Typically, IE would warn you when DNS-based information conflicts with the security certificates involved in the SSL transactions. Unfortunately, this verification can break down when the connection to a secure server is made via an image or frame. IE also fails to revalidate certificates within the same session.
It’s important to keep IE (and other browser) patches up to date by checking periodically with the browser maker. There are, however, other things you can do to help yourself even beyond the patches.
One immediate thing you can do when connected to an SSL site is to check the name recorded in the site’s certificate to make certain it’s what you expect. In IE5 double click on the padlock. In the dialog that appears click on the “Details” tab to see certificate information. If anything appears out of order, be suspicious before sending any personal information.
For even more confidence you can validate certificates independently. Using the technique above you can obtain the certificate fingerprint and, by calling the issuing organization, you can verify the fingerprint matches the site you think you are sending information to. You can also delete all certificates to cause them to be revalidated every time you encounter one. A pain, but this gives you maximum control.
Some browsers do not have a mechanism for validating certificates. If yours is one of those, you should consider using a different browser.
MS Security. Microsoft has issued a few new security bulletins this past month. Below is a summary (this is only a summary for Windows 95/98; it does not include NT–see the Microsoft web site for a complete listing):
- “Frame Domain Verification”, “Unauthorized Cookie Access”, and “Malformed Component Attribute” Vulnerabilities. Patches for three unrelated problems in the same DLL file used by IE 4 and 5.
- “IP Fragment Reassembly” Vulnerability. The vulnerability could be used to cause an affected machine to lock up.
- “Protected Store Key Length” Vulnerability. Could make it easier for a malicious user who had complete control over a Windows 2000 machine to compromise users’ sensitive information.
- “HTML Help File Code Execution” Vulnerability. The HTML Help facility provides the ability to launch code via shortcuts included in HTML Help files. If a compiled HTML Help (.chm) file were referenced by a malicious web site, it could potentially be used to launch code on your computer.
- “SSL Certificate Validation” Vulnerabilities. (See above article.)
- “Desktop Separation” Vulnerability. A Windows 2000 patch that fixes a vulnerability that would allow a hacker to gain added privileges if the hacker had keyboard access.
For all of these items and more please take a look at:
http://www.microsoft.com/security/default.asp![]()
General Interest
Y2K Revisit. Now that six months have about passed since the magic transition from 1999 to 2000 with all the surrounding hype, if you’re at all interested in finding out what really happened there are a couple of web sites that have been tracking the various problems. For a list of Y2K problems take a look at:
[Link 404]
If you want to actually see screen shots of various glitches take a look at:
[Domain taken down.]
Virus News
If you have not taken a look at the Computer Knowledge Virus Tutorial lately, please come back and take a new look. It’s been reorganized, streamlined, updated and it’s still free with a PDF download available so you can read it at your leisure off-line.
More complete descriptions of most of these viruses can be found at the Sophos web site:
http://www.sophos.com/virusinfo/analyses/![]()
Trojans. These important new Trojans appeared recently:
- Downloader (Badman). This example of a dual-extension Trojan is yet another example of why you need to be particularly careful about what you download and then execute on your system. The file, called “QUICKFLICK.MPG.EXE” is supposed to be a movie file. On systems with viewing extensions suppressed the file will look like a movie file as you won’t see the “.EXE” part of the name (however, the fact that you do see an extension on such a system should be a red flag anyhow!). When executed, the program (it’s not a movie) attempts to connect to a website and download a second program which turns out to be a backdoor Trojan (Subseven by some reports) capable of not only sending information about you to those controlling the program but also capable of turning your computer into a zombie capable of participating in distributed denial-of-service attacks without your knowledge. The beast was discovered when its perpetrators conducted a brief test; the results of which were observed by security experts. There are varying reports of numbers of computers already infected around the world. Most infected are reported to be on high-speed connections (e.g., ADSL or ISDN). This is something to watch out for as more and more home users connect to such links but fail to take necessary firewall precautions.
Macro Viruses. A number of macro viruses have been announced this past month. Below is a summary of the more important ones:
- WM97/Akuma-D. A complex Word macro virus that activates on some randomly-selected day within 30 days of infection. A message box is displayed and the C:, D:, and E: drives deleted. The message box will have one of a variety of preprogrammed titles.
- WM97/Ciao-A. Inserts various text into documents based on complex date calculations. Also inserts “Caio!!!” into documents when they are closed.
- WM97/IIS-U. A changing (polymorphic) macro virus. Variable names are randomly created and random instructions are included in the virus each infection. Not all created viruses work.
- WM97/Marker-AO, DJ, and DW. Marker variants that send document summary information to the Codebreakers site. They also display various message boxes.
- WM97/Melissa-BE. Yet another Melissa macro virus knockoff.
- WM97/Now-A. A replicating-only Word macro virus that puts random comments into its code as a means of avoiding detection.
- WM97/Resume-A. A hyped macro virus that never seemed to spread very far. Basically, the virus is attached to an E-mail with the subject “Resume – Janet Simons” and the body of the message indicating the attachment is a resume directed to the “Director of Sales/Marketing.” If opened, the attachment would send itself to others in your Outlook address book and then delete a number of files. It would also copy itself to your Startup directory as the file EXPLORER.DOC.
- WM97/Smac-E. This beast needs a double-byte language version of Word.
- WM97/Thursday-W and Z. Thursday variants that attempt to delete the C: drive on 13 December.
- WM97/Vmpck1-DM. Activates if Word’s About box is opened after Word has been running for over five hours. Also activates if you attempt to access the macro code. In this latter case it drops and attempts to run a program.
- XM97/Barisada-A. An Excel macro virus with all macros stored in the file HJB.XLS. When activated (24 April from 2pm to 3pm) you are taken through a variety of dialog box questions in the form of a game. A wrong answer may result in all open worksheets being cleared.
- XM97/Jini-A. An Excel virus. It has various activation effects. It might, for example, delete all sheets in a workbook except the active sheet. It may also rename items in the File menu. It also sometimes displays a message box.
- XM97/Yawn-A. An Excel macro virus with an infection method similar to the Word macro virus Bridge-A.
Worms. A number of worms have been announced this past month. Below is a summary of the more important ones:
- Timofonica. Widely reported as a cell phone virus, this is nothing close to that. Basically, it is yet another dual extension worm, where this time the file attached to an E-mail is named “TIMOFONICA.TXT.VBS.” Run, the script will write the file CMOS.COM to your System directory and edit the registry to run the file. When run CMOS.COM will attempt to overwrite CMOS and delete the hard disk partition tables. The worm will also send a copy of itself to your Outlook address book and a text message to some users of Telefonica’s (Spain’s) mobile phone service. This is what caught the attention of the press. Otherwise, Timofonica is fairly standard and did not spread widely since all messages were in Spanish.
- Gnutella Worm. Gnutella is a file-sharing network where members running the Gnutella software make certain files and/or directories available to anyone else on the Internet running the same software. It’s typically been used to trade movie and MP3 files. Unlike Napster, which generally is limited to MP3 files, Gnutella can be used to transfer any file type. What is being called the Gnutella Worm can be found in a number of aliases. Common ones include: “GLADIATOR.VBS”, “COLLEGESEX.VBS”, or “NAPSTER METALLICA CRACK.VBS”. Like any other program that you download or transfer from any source you must be careful about running any executable file. These are no different. At the moment, the first of these worms does no damage; it just makes itself available to spread. There are, however, any number of things that could be programmed into the next one. Be careful what you download and execute!
- VBS/NewLove-A. A takeoff on the Loveletter worm that mutates as an attempt to avoid detection. On execution the worm creates a copy of itself with a random name (selected from your \Windows\Recent folder renamed with a .VBS extension) and then forwards that copy to everyone in your Outlook address book. The message subject is “FW: <name>” where <name> is the original name of the file being hijacked. There is no message text. The beast further attempts to set all local and remote files to zero length. This is worse than deleting the files since the pointers to the file start are erased in this process and the files generally can’t be easily recovered. The worm did not spread widely since it increases in size on each mutation with an associated slowdown in the mail servers; allowing it to be stopped.
- VBS/Fireburn-A. A Visual Basic Script worm that spreads via Outlook E-mail and mIRC (Internet Relay Chat). The worm sets itself up to run at system start using the file \Windows\RUNDLL32.VBS. It looks for an mIRC client and overwrites the SCRIPT.INI file that sends itself to people via your client. It also E-mails itself to your Outlook address book. The attached worm file is named with a sexually suggestive name to entice others to open it. The worm is also bilingual in that it checks for a C:\PROGRAMME directory. If it exists the message will be in German; otherwise in English. On 20 June it will display a message box announcing its presence. On the next system start the keyboard and mouse will be disabled. Fireburn does not seem to be widespread.
- VBS/CoolNote-A. Another double-extension worm that attempts to get you to open an E-mail attachment. The E-mail has the subject “Cool Notepad Demo” and the attachment name is “COOL_NOTEPAD_DEMO.TXT.VBS”. CoolNote does not seem to be widespread.
- VBS/Scrambler & W32/Scrambler. A Visual Basic Script worm and Win32 executable file virus. The E-mail containing the virus has the subject “Check this out, it’s funny!” and an attached file with a random five-character (A to J) rootname and .EXE extension. The EXE file will infect other EXE files in the Windows directory and the C:\mIRC\Downloads directory. Also, if the mIRC directory is found the SCRIPT.INI file will be changed to send a VBS version of the virus to the first 90 entries in your Outlook address book and then delete itself. The virus also makes MP3 files sound like scratched records. Finally, it displays a message on system start.
- VBS/LoveLet-AS. Yet another of the many Loveletter clones. This one purports to have Presidential and FBI secret pictures in the attached file (a variant simply forwards random characters so you really don’t know what it’s trying to sell). The worm attempts to download three files: MACROMEDIA32.ZIP, LINUX321.ZIP and LINUX322.ZIP. These are really a text file and two graphic files (irrespective of their names). The text file is saved in your Windows directory as IMPORTANT_NOTE.TXT and the two graphic files replace your startup and shutdown pictures: LOGOS.SYS and LOGOW.SYS. The worm further copies itself to LINUX32.VBS and RELOAD.VBS and sets itself to run at system start. Finally, it make another copy of itself in your System directory with a random rootname and extension of either .GIF.VBS or .JPG.VBS. This is the file that gets sent out via E-mail to others.
In closing: Thanks to all those who made the conversion from the mailing list I maintained to listbot.com.